How to store encryption keys c images are ready in this website. How to store encryption keys c are a topic that is being searched for and liked by netizens now. You can Find and Download the How to store encryption keys c files here. Download all royalty-free images.
If you’re looking for how to store encryption keys c pictures information connected with to the how to store encryption keys c interest, you have pay a visit to the right site. Our site frequently provides you with hints for refferencing the maximum quality video and picture content, please kindly search and locate more enlightening video articles and images that match your interests.
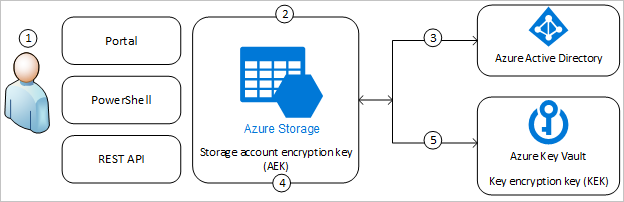
For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption. For more information about the default cloud-based tenant root keys. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data. For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption. Ive seen plenty of encryptiondecryption tutorials and examples on the net in C that use the SystemSecurityCryptographyRSACryptoServiceProvider but what Im hoping to be able to do is.
How To Store Encryption Keys C. For more information about the default cloud-based tenant root keys. Odk Additionally you can provide keys from arbitrary filesystem locations via the respective cmdline switches. Encryption is a process to change the form of any message in order to protect it from reading by anyone. Symmetric Key Encryption.
 Skater Net Obfuscator To Protect Windows Store Application Microsoft Visual Studio Grid App Net Framework From pinterest.com
Skater Net Obfuscator To Protect Windows Store Application Microsoft Visual Studio Grid App Net Framework From pinterest.com
Odk Additionally you can provide keys from arbitrary filesystem locations via the respective cmdline switches. For more information about the default cloud-based tenant root keys. In Symmetric-key encryption the. RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. It is public key cryptography as one of the keys. Encryption is a process to change the form of any message in order to protect it from reading by anyone.
RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices.
In Symmetric-key encryption the. For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption. Symmetric Key Encryption. RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. It is public key cryptography as one of the keys. In Symmetric-key encryption the.
 Source: edument.se
Source: edument.se
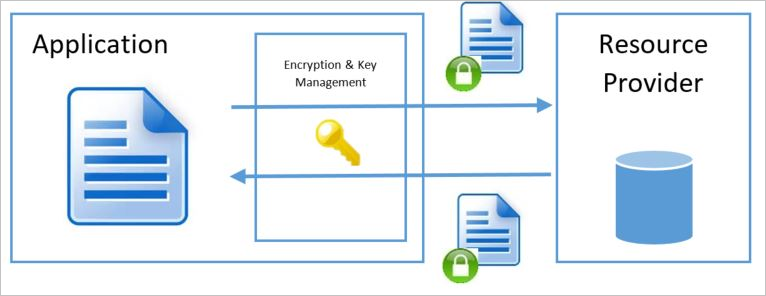
It is public key cryptography as one of the keys. Double Key Encryption supports both cloud and on-premises deployments. Odk Additionally you can provide keys from arbitrary filesystem locations via the respective cmdline switches. RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. It is public key cryptography as one of the keys.
 Source: docs.microsoft.com
Source: docs.microsoft.com
For more information about the default cloud-based tenant root keys. It is public key cryptography as one of the keys. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data. RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption. In Symmetric-key encryption the.
 Source: syncfusion.com
Source: syncfusion.com
RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. Symmetric Key Encryption. Odk Additionally you can provide keys from arbitrary filesystem locations via the respective cmdline switches. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data.
 Source: pinterest.com
Source: pinterest.com
In Symmetric-key encryption the. For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption. Encryption is a process to change the form of any message in order to protect it from reading by anyone. It is public key cryptography as one of the keys. Symmetric Key Encryption.
 Source: docs.microsoft.com
Source: docs.microsoft.com
Symmetric Key Encryption. Double Key Encryption supports both cloud and on-premises deployments. For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption. In Symmetric-key encryption the. It is public key cryptography as one of the keys.
 Source: pinterest.com
Source: pinterest.com
RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption. Symmetric Key Encryption. In Symmetric-key encryption the. Encryption is a process to change the form of any message in order to protect it from reading by anyone. For CIK it is not important how the keys are named if they have the binary structure of 16 byte encryption.
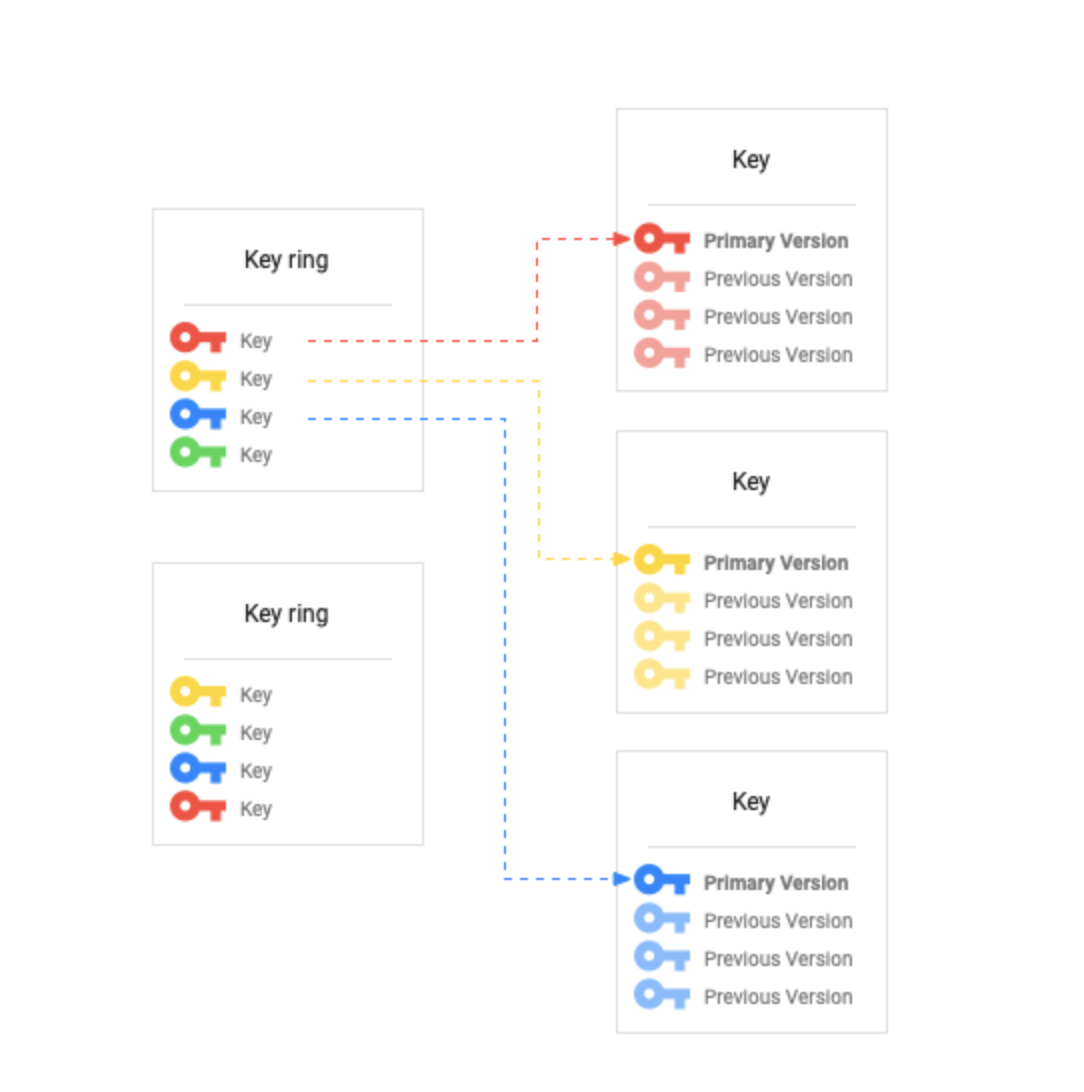 Source: jayendrapatil.com
Source: jayendrapatil.com
Ive seen plenty of encryptiondecryption tutorials and examples on the net in C that use the SystemSecurityCryptographyRSACryptoServiceProvider but what Im hoping to be able to do is. Symmetric Key Encryption. RSA Algorithm is used to encrypt and decrypt data in modern computer systems and other electronic devices. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data. In Symmetric-key encryption the.
 Source: medium.com
Source: medium.com
Symmetric Key Encryption. Double Key Encryption supports both cloud and on-premises deployments. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data. Symmetric Key Encryption. In Symmetric-key encryption the.
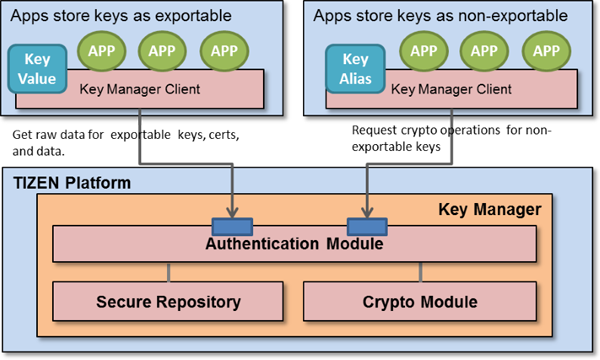 Source: docs.tizen.org
Source: docs.tizen.org
In Symmetric-key encryption the. Ive seen plenty of encryptiondecryption tutorials and examples on the net in C that use the SystemSecurityCryptographyRSACryptoServiceProvider but what Im hoping to be able to do is. Double Key Encryption supports both cloud and on-premises deployments. Symmetric Key Encryption. RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption.
 Source: pinterest.com
Source: pinterest.com
RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption. Ive seen plenty of encryptiondecryption tutorials and examples on the net in C that use the SystemSecurityCryptographyRSACryptoServiceProvider but what Im hoping to be able to do is. RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption. In Symmetric-key encryption the. These deployments help to ensure that encrypted data remains opaque wherever you store the protected data.
 Source: codeproject.com
Source: codeproject.com
RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption. In Symmetric-key encryption the. Symmetric Key Encryption. It is public key cryptography as one of the keys. RSA algorithm is an asymmetric cryptographic algorithm as it creates 2 different keys for the purpose of encryption and decryption.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how to store encryption keys c by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.